
Energy Theft and Fraud Reduction
Jun 17, 2020Power theft is the menace of electric utilities from rural cooperatives to large investor-owned and municipal providers. Utility companies have been plagued with non-technical losses almost since their inception. As early as 1899, the Association of Edison Illuminating Companies addressed the problem of tampering with screws that adjusted meter damping magnets.
Over 36 years ago in 1984, the New York Times published an article1 citing ConEd and the potential of "1% of power customers of stealing services." As power generation and electric utility proliferation moved into developing countries, many more providers confronted new challenges and obstacles to combat non-technical losses and the issues it causes. No utility provider is immune to attempts to steal power.
The financial losses, also known as non-technical losses, include metering inaccuracy, non-payment, billing, and rate class errors and simple to complex energy theft. The two dominant components of non-technical losses are non-payment and energy theft.
Non-payment refers to customers who are unable or unwilling to pay for their electricity, which can lead to significant revenue loss if the utility fails to handle nonpayment situations quickly. However, electricity theft usually impacts a utility more than non-payment problems.
Until recently, there were few effective solutions for this problem. Labor-intensive premise inspections and account auditing often costs more than the actual value of the losses, enforcement is always challenging, and previously Advanced Metering Infrastructure (AMI) was not cost effective in many countries. Regulators typically do not require utilities to absorb the costs. Instead, electricity ratepayers subsidize the thievery. So non-technical losses are often hidden costs and have received little public attention, but they have enormous costs for utilities, customers and governments. The idea that energy theft is a victimless crime is clearly wrong.
According to estimates, theft and fraud of electricity costs the industry as much as $96 billion2 every year globally, with as much as $6 billion3 every year in the United States alone. This $96 billion global problem not only results in higher prices for paying customers and costly government subsidies but is also a public safety crisis in some countries with dangerous illegal power connections. In many countries, high non-technical losses threaten the financial sustainability of the energy utilities.
Meanwhile the issue of theft and fraud leaves utility managers with a powerless feeling in their ability to prevent or confront the issue. However, this trend is rapidly changing. Utilities now have many tools to reign in losses and detect unauthorized theft and fraud before it creates a significant drain on resources and company revenue. Many of these tools are provided through the installation of AMI and the additional visibility of the low-voltage grid that these systems provide.
Non - technical Losses
They are caused by actions external to the power system and consist primarily of electricity theft, non - payment by customers, and errors in accounting and record - keeping.
Metering and billing for electricity actually consumed by users is integral to commercial management of an electricity utility.
Background
Electricity theft is nothing new and can be a complex phenomenon with many facets. Theft of power is common in many countries and a considerable amount of energy is stolen every year from the electric low voltage grid. An electric utility low voltage grid can never be one hundred percent secure from theft and fraud due to the number of distributed end points which sit largely unmonitored in public accessible locations.
The problem has socioeconomic, political, environmental and technical roots, but the solution is generally sought solely through technical measures. In many systems the amount of energy theft is relatively small (1–2%) in terms of the electricity generated. But, the financial loss is high due to the large amount of electricity being distributed.
The financial losses are critical to many electric power utilities. Lost earnings can result in lack of profits, shortage of funds for investment in power system capacity and improvement, and a necessity to expand generating capacity to cope with the non-technical losses. Some electric utility companies in the worst affected countries are near bankrupt from the impact of year over year losses.
Many electric utilities are embarking on specific programs to reduce electric energy losses on their low voltage grids, both as a measure of energy conservation and as an alternative to adding generation capacities. One of the primary sales drivers for advanced AMI systems during the last few years has been the potential to reduce non-technical losses from a theft and fraud prospective. The upward industry trend seems to be that more and more utilities seek the ability for much more stringent practices in theft detection and ability to discover fraud.
Types of Theft and Frauds
There are four types of “theft/Fraud” prevalent in all power low voltage grid systems. The extent of the theft will depend upon a variety of factors—from cultural to how the power utility is managed.
1. Fraud - Fraud is when the consumer deliberately tries to deceive the utility. A common traditional practice is to manipulate or physically tamper with the meter so that a lower readings of power use are shown than is the actual consumption case.
Consequently, in new smart AMI technology systems, usage data may be vulnerable to being tampered with before/after recording or in transmission to utilities. Moreover, software -based attacks often require less expertise to execute and thus are likely to have the potential to be more widespread and frequent into the future.
Precedence and history have shown that these types of software attacks are quickly monetized by criminal organizations, often disguised as legitimate businesses that sell the hardware and software needed for theft of service.
For instance, look at the Black-box tone generator of the 1980’s providing the ability to make free local and long distance calls by using a cheaply made device to generate the phone switch tones necessary to steal service. Then, in the 1990’s, came the cable television descrambler box that lead to over $4 billion in cable theft per year, and currently, there are websites that sell SIM unlock codes for cellular phones.
Often, these organizations use a cash only or digital cryptocurrencies to process transactions affording them anonymity and a difficult traceable money trail.
2. Stealing Electricity - Electricity theft can be arranged by rigging a line from the power source to where it is needed, bypassing the meter. In Mexico, there have been a high volume of illegal customers, who steal electricity with wires known as pequeño diablos or ‘little devils.’ The illegal lines are easy to detect as they are often above ground and highly visible. However, reports of utility staff being assaulted and needing police security to carry out the removal of the lines are common place. Published reports say the theft in Mexico result in the yearly loss of as much as $1.3 billion4 in revenues annually.
Corrupt staff from the electricity organization may take bribes to allow the practice to continue. On a larger scale, businesses may bribe power organization staff to rig direct lines to their buildings or offices and the power does not go through a meter. Money also can be given to inspectors to keep them from finding and/or reporting the theft.
3. Billing Irregularities – This can occur from several sources. Some power organizations may not be very effective in measuring the amount of electricity used and unintentionally can give a higher or lower figure than the accurate one. The unintentional irregularities may even out over time. However, it is also very easy in some systems to arrange for much lower bills to be given than for the power actually used.
Employees may be bribed to record the meter at a lower number than is shown. The consumer pays the lower bill and the meter-reader earns unofficial salary. In another type of billing irregularity, office staff can move the decimal point to the left on the bill so that a person or company pays $47.48 instead of $474.80. Consumers may know that some power organization staff are ‘‘on-the-take’’ for providing these services.
4. Unpaid Bills - Some people and organizations do not pay what they owe for electricity. Residential or business consumers may have left the city or an enterprise has gone bankrupt. Some systems have chronic non-payers—the very rich and politically powerful who know that their electricity will not be cut regardless of whether they pay or not. An example of this could be an airport in an exotic tourist destination, that owes the utility millions of dollars in debt, yet because of the nature and necessity of the business of tourism and the effects on the overall economic impact, this loss rarely is looked at as theft.
The Energy Thief
1. Customers - Traditionally, customers have been the primary attack group aimed to steal electric power. The limited means and motivation to tamper with analog meter devices is very much individual in nature. That said, customers are limited in their resources and technical abilities, but in the case of all AMI systems, information can readily be shared over the Internet, and also customers can distribute some of the labor in discovering vulnerabilities and designating attacks to members of organized crime businesses with a simple purchase.
2. Organized Crime (Businesses) - The motivation in the case of these “Business” organizations is the monetization of energy theft. This comes in various forms such as Marijuana growers, who steal electricity to monetize and increase profits from their operations, through to “free power consumption” for “clients” of the criminals.
Other criminal organizations seek to exploit the extended computing and network capabilities of smart AMI technologies. The task of creating software and hardware tools to compromise smart meter devices and other infrastructure hardware can be offloaded from the customers to professional hacker organizations for profits.
Members in this group will leverage certain design aspects of AMI technology systems, such as the widespread use of the same password set over many meters, to greatly amplify the profit from cracking a single meter.
3. Utility Insiders - These are employees who are implicitly trusted to be honest in the case of analog meters and the same model usually applies for smart AMI technology. Often, unscrupulous utility employees who have access to privileged information of device vulnerabilities cannot resist the temptation to make a few extra dollars on the side off their employer. While we often see this more frequently in socioeconomically depressed countries, the potential for a rogue utility employee is market wide.
4. Nation States - Global adversaries with this level of expertise and infinite resources have very little motivation to commit theft of energy as examined in this document. However, they may use discovered smart meter vulnerabilities from other theft entities outlined here for the denial of data services or widespread electric service outages, so they are worth noting. Further examination of these types of threats would fall more on intrusion detection security aspects.
The Attack Field
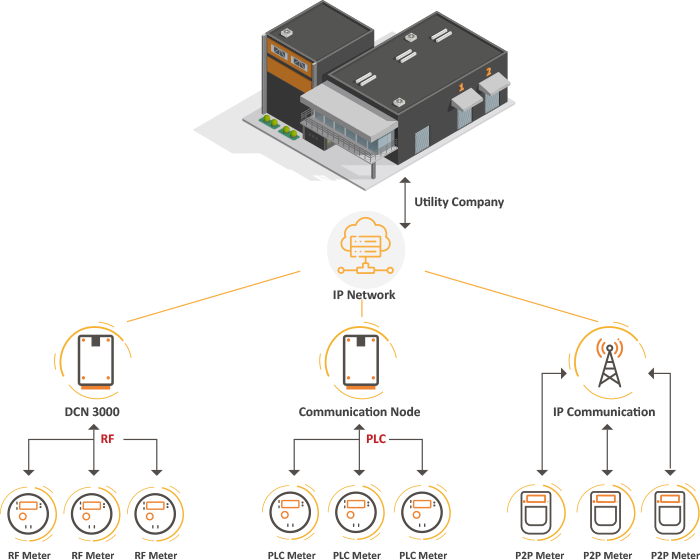
This is an example of the typical utility AMI deployment with a mixed combination of Power Line Communication, RF Mesh and Point to Point devices containing a direct cellular modem device for communication. All devices get connected through a backhaul communication network with IP based functionality either by the utility or a third-party network provider.
1. Meter Devices – Are the most vulnerable piece of the utility device deployment. Just as with traditional analog devices, these devices can be physical manipulated and attacked for theft of services. Beyond the physical manipulation these devices can be subject to software manipulation through undetected or unknown vulnerabilities. Point to Point meter devices can be subject to third party data security practices and subject to attack elements beyond the scope of this document.
2. Communication Nodes – Are usually secure at the utility company’s facility or located in proximity to the transformer location in a located ruggedized case. While these devices are usually pretty safe from customer based physical manipulation attacks, with smart AMI systems they are still vulnerable to software-based attacks and potential data manipulations. In some emerging markets, the physical security around these nodes may be lacking, and so these nodes can also be subjected to physical attack which can include using their physical ports to initiate cyber-attack activities
3. IP Networks – All smart AMI systems rely on IP based networks to provide back haul network connectivity services of data from the meter to the Utility. This presents a unique challenge for security and theft prevention. While most Smart AMI systems use some form of encryption based security on network data packets being transmitted, with the proper credentials this data can be manipulated and changed prior to the transmission phase, even if the meter has not been physically tampered with.
Traditional meter tamper detection mechanisms were limited to locks and tamper-evident seals. While these measures are often sufficient for keeping honest people honest, they offer little to deter malicious tampering, and are often circumvented without the utility knowing.
Modes of Attack
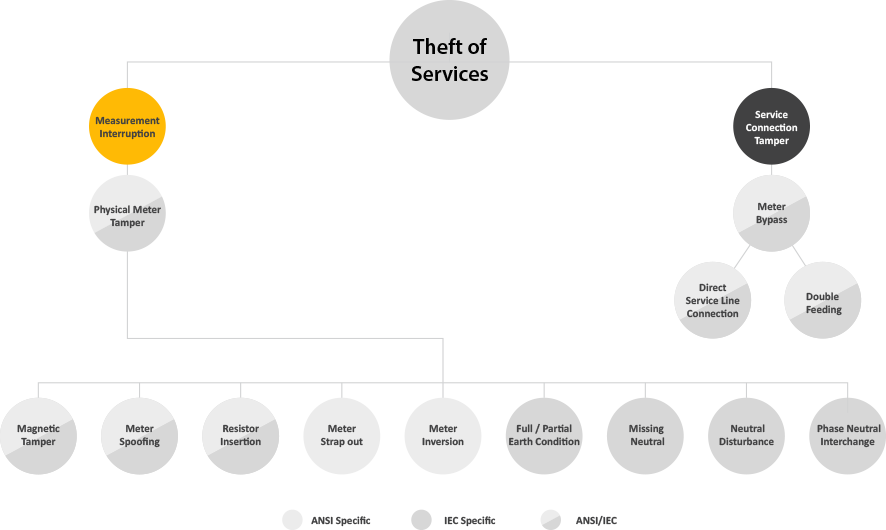
This diagram describes the attack vectors for theft of energy services. As shown, there are several attack vectors that providers need to consider in order to adequately provide the necessary security and ability to detect theft and non-technical losses. Potential attacks include the following:
1. Measurement Interruption
Physical Meter Tamper – Manipulation of the physical meter device.
- Magnetic Tamper – Applying a rare earth magnet to attempt to manipulate consumption usage.
- Meter Spoofing – Moving smart meter to another no active meter housing off the house and replacing with other non-utility meter hardware.
- Resistor Insertion – Wiring in a resistor into the meter metrology to slow down the calculations of consumption.
- Meter Strap out – Appling wires to the rear of the meter connecting the service line and the home energy input.
- Meter Inversion – Flipping the meter upside in the meter socket or wiring the IEC meter backwards.
- Full or Partial Earth Condition – One of the loads is connected to earth and the other is returned back to neutral of the meter.
- Missing Neutral – Condition occurs when the neutral is disconnected from the meter.
- Neutral Disturbance – Similar to Missing Neutral that apart from tampering with the neutral at the source.
- Missing Potential – Voltage for one phase is made zero by removing one of the phase wires.
- Phase and Neutral Interchange – Phase and Neutral of meter are interchanged, reverse current flow.
2. Service Connection Tamper
Meter Bypass – Physically bypassing the meter completely
- Service Line Connection – Direct connection to the service line bypassing disconnected or missing meter and consumption recording.
- Double Feeding - Direct connection to the service line bypassing a legal meter service to feed devices not recorded by legal meter consumption.
- Optical Bypass - Monitoring software on an external device can be used to capture the optical port protocols used to communicate with the meter and potentially capture the device password. Once the meter is opened, placing a reading device on the optical port pins or near the optical lens is sufficient for capturing the password amidst the rest of the protocol. Furthermore, the data could be identifiable with significant time to investigate the meter tables and data on the meter once a password is obtained.
Examples of potential measurement interruption scenarios:

Magnetic Tamper
Physical Meter Tamper

Resistor Insertion
Physical Meter Tamper

Meter Strap Out
Physical Meter Tamper

Meter Inversion
Physical Meter Tamper
Defining measurement interruption scenarios:

Direct Service Line
Connection – Service Connection Tamper

Double Feeding
Service Connection Tamper
Conclusions
- Non-technical losses have plagued utilities since their inception and are now a global problem for electric providers to the sum of $96 billion dollar a year in lost revenue.
- Non-technical losses are derived from socioeconomic, political, environmental and technical roots, but the end solution is generally sought solely through technical measures.
- Criminal enterprise usually increases profits through energy service theft and creates unsafe situations for grid stability.
- Non-technical losses drive up costs for the consumers and cut into the utility’s revenue and over all bottom line.
- One of the primary sales trends for smart AMI meter system throughout the industry has been the potential to reduce non-technical losses related to theft and fraud.
- AMI solutions help to limit many of the opportunities for theft and fraud, but also expose new opportunities, especially to the cyber-criminal. A deployment of an AMI solution must be combined with a realistic assessment of those theft and fraud opportunities, which will be left open and any new opportunities that can be introduced.
- Detection of theft and fraud is difficult, even with an AMI solution, as the indicators of theft and fraud may be hidden behind “false positives”. Such detection is often beyond the resources of the operations team of a utility.
The NES Advantage
The NES AMI solution provides a robust platform with many features designed to protect utilities from fraud and theft including alarms for tampering, power-cycles, cover removal, and other indicators of fraud and theft.
Having an AMI platform that is aware of these types of activity is just one part of the story. The challenge beyond this is two-fold:
• To receive these indicators in a system that makes it possible to identify the events
• Identify incidents that relate to fraud and theft, both on a specific meter, but also in connection with a wider and systematic fraud and theft campaign.
NES Grid Operations and Grid Watch provide advanced analytics and threat detection that have been developed for specific low-voltage smart grid security threats and attacks. The software identifies specific types of security incidents :
Grid Operations provides visual insight for the utility as a single point for alerts and events pertaining to fraud and theft of services on the low voltage grid. Filtering rules can be applied to events from meters or groups of meters to identify sequences of events, which may be indicative of intentional fraud and theft activity in the low-voltage grid.
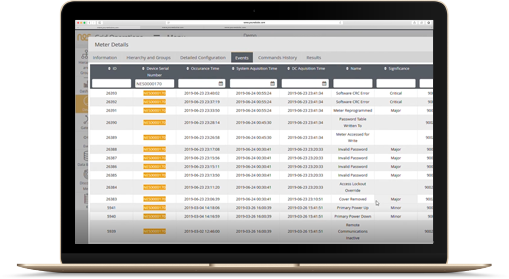
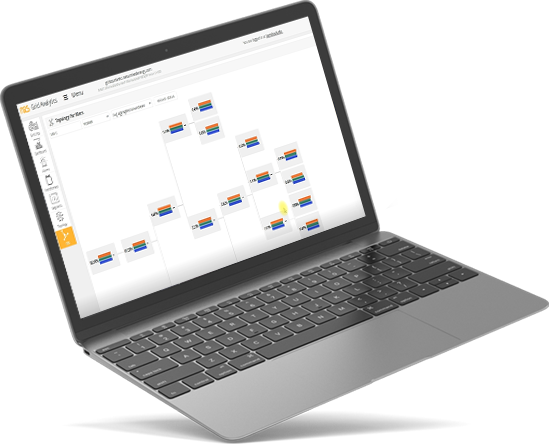
Grid Navigator and Grid Flow provide a view of low-voltage grid topology upon which energy flows can be superimposed, providing visibility of potential points of energy theft and fraud within the low-voltage grid, not just at consumer end-points.
Grid Watch provides AMI cyber-security threat detection by closely monitoring attacker behaviour in the grid and alerting utility incident response teams before, during, and after a successful cyber-attack.
These capabilities are deployed out-of-the-box and immediately available – there is no need to enter a major development program to create these analytics capabilities.
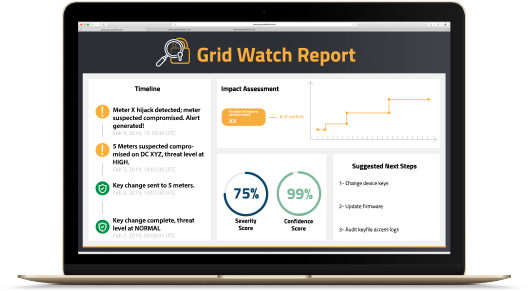
Through NES Hardware and software, the utility obtains visibility of the activities of theft, fraud, and cyber-attacks for multiple attack scenarios including:
• Physical device tamper alarms such as cover removal, device tilts, and magnetic fields.
• In addition to magnetic tamper alarming, meters offer immunity to severe magnetic tampering attempts.
• Neutral metering and disconnection
• Load-side bypass checking
• Denial of service and device power cycles
• Derailment of operational and business algorithms, Billing, Operations
• Ransom, of customer information, of corporate information, of assets and of service.
Reference
1. Utilities Say 1% of Users Are Stealing Power
https://www.nytimes.com/1984/03/26/us/utilities-say-1-of-users-are-stealing-power.html
2. Electricity theft and non-technical losses total $96bn annually -
https://www.smart-energy.com/regional-news/africa-middle-east/electricity-theft-96bn-annually/
3. Energy Theft: A Growing Problem
https://www.distributedenergy.com/home/article/13024533/energy-theft-a-growing-problem
4. Authorities are going after petroleum thieves; will electricity thieves be next?
https://mexiconewsdaily.com/news/electricity-thieves/











